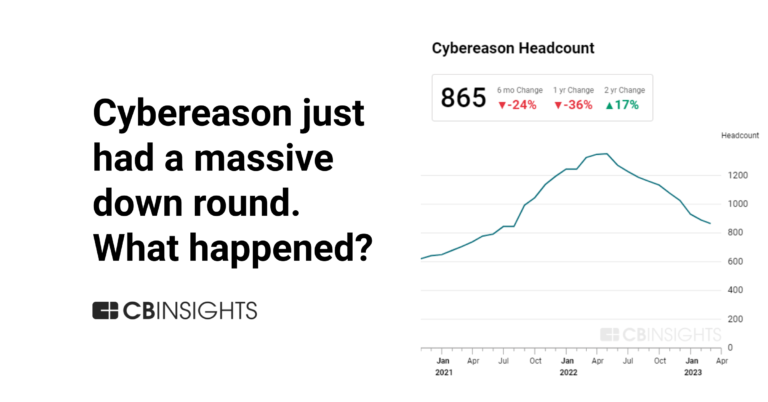
Cybereason
Founded Year
2012Stage
Valuation Change | AliveTotal Raised
$813.62MRevenue
$0000Mosaic Score The Mosaic Score is an algorithm that measures the overall financial health and market potential of private companies.
-65 points in the past 30 days
About Cybereason
Cybereason specializes in cybersecurity solutions. It facilitates threat detection and response, ransomware protection, and proactive threat hunting, all designed to provide comprehensive protection against cyber attacks. Its primary customers are businesses and organizations across various sectors that require robust cybersecurity measures. It was founded in 2012 and is based in Boston, Massachusetts.
Loading...
Cybereason's Product Videos
ESPs containing Cybereason
The ESP matrix leverages data and analyst insight to identify and rank leading companies in a given technology landscape.
The threat intelligence platforms market offers solutions to address the challenges faced by security teams in protecting their organizations from cyber threats. These platforms aggregate and correlate data from various sources, including internal security logs, external threat feeds, dark web monitoring, and open-source intelligence. The data is enriched with AI to create profiles & patterns of m…
Cybereason named as Challenger among 15 other companies, including CrowdStrike, Tata Consultancy Services, and Splunk.
Cybereason's Products & Differentiators
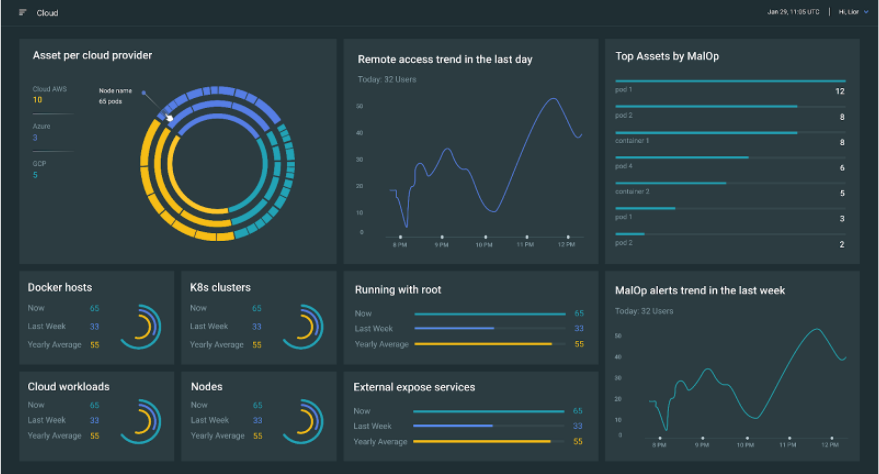
Cybereason XDR
Cybereason XDR, powered by Google Cloud, automates prevention, detection and response for complex cyberattacks as it guides analysts through security operations and incident response, enabling proactive threat hunting with precision at a pace never before achieved:
Loading...
Research containing Cybereason
Get data-driven expert analysis from the CB Insights Intelligence Unit.
CB Insights Intelligence Analysts have mentioned Cybereason in 5 CB Insights research briefs, most recently on Nov 21, 2023.
Nov 21, 2023
Has the global unicorn club reached its peak?
Nov 3, 2023
The endpoint security market map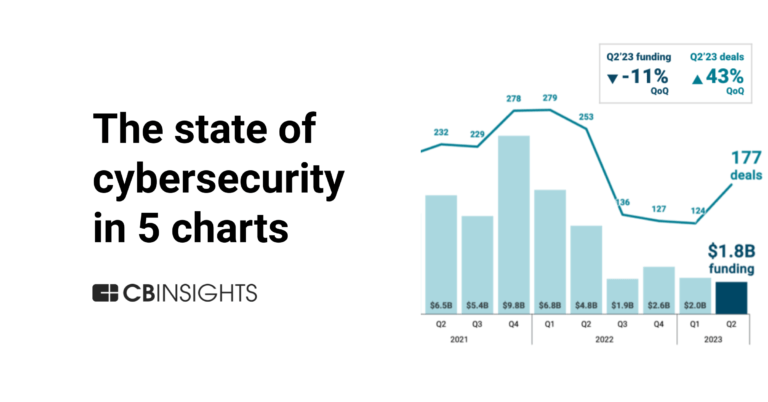
Sep 28, 2023
The state of cybersecurity in 5 chartsExpert Collections containing Cybereason
Expert Collections are analyst-curated lists that highlight the companies you need to know in the most important technology spaces.
Cybereason is included in 7 Expert Collections, including AI 100.
AI 100
99 items
Winners of CB Insights' annual AI 100, a list of the 100 most promising AI startups in the world.
Artificial Intelligence
14,767 items
Companies developing artificial intelligence solutions, including cross-industry applications, industry-specific products, and AI infrastructure solutions.
Tech IPO Pipeline
282 items
Track and capture company information and workflow.
Conference Exhibitors
5,302 items
Cybersecurity
9,652 items
These companies protect organizations from digital threats.
Targeted Marketing Tech
206 items
Cybereason Patents
Cybereason has filed 26 patents.
The 3 most popular patent topics include:
- computer security
- computer network security
- cyberwarfare
Application Date | Grant Date | Title | Related Topics | Status |
|---|---|---|---|---|
11/10/2021 | 9/3/2024 | Computer security, Cyberwarfare, People associated with computer security, Strategy, Cognitive science | Grant |
Application Date | 11/10/2021 |
|---|---|
Grant Date | 9/3/2024 |
Title | |
Related Topics | Computer security, Cyberwarfare, People associated with computer security, Strategy, Cognitive science |
Status | Grant |
Latest Cybereason News
Aug 26, 2024
eSecurity Planet content and product recommendations are editorially independent. We may make money when you click on links to our partners. Learn More . The best alternative solutions to CrowdStrike Falcon are endpoint security and endpoint detection and response (EDR) platforms that help detect and prevent malicious threats. Security products focused on protecting endpoints offer features like device controls, vulnerability management, and threat hunting. If you’re looking for an alternative solution to CrowdStrike, I’ve compared popular solutions in the industry and narrowed them down to the best. Here are the six best alternative solutions to CrowdStrike Falcon: Bitdefender GravityZone : Best for small business budgets Table of Contents Top CrowdStrike Alternatives Compared The following table compares a few features of CrowdStrike’s major competitors and the availability of a free trial. Behavioral Analytics ✔️ = yes ❌ = no ➕ = add-on While these solutions are the best in the endpoint detection market, I found that Palo Alto Cortex XDR was the best overall platform to replace CrowdStrike Falcon. Continue reading to learn more about these products, or skip down to see how I evaluated the best EDR alternatives to CrowdStrike. Palo Alto Cortex XDR – MITRE scores: 5/5 Customer support: 4.5/5 Palo Alto Cortex XDR is a highly advanced security platform for protecting endpoints across your business infrastructure. Palo Alto Networks is renowned for its excellent security — it most recently posted perfect scores in the MITRE ATT&CK evaluations — and like CrowdStrike, it offers advanced features like custom detection rules and incident triage. I recommend Palo Alto for experienced teams that need top-notch security and can manage a large platform. Cons May be complex for smaller teams to use No free trial Free demo: Contact to schedule Key Features Forensics: Cortex XDR investigates incidents involving endpoints even when they aren’t connected to the network. Root cause analysis: Palo Alto allows admins to examine the root causes of incidents and the sequence of events leading to them. Behavioral analytics: The platform analyzes threat trends and malicious behavior to detect malicious insider attacks and credential abuse. Incident prioritization: Cortex XDR prioritizes fixing incidents by grouping alerts and scoring the incidents. Screenshot Alternatives Although Palo Alto Cortex XDR is a great security solution for enterprises, it will take less experienced teams significant time to learn and use effectively. If you need an easier-to-use platform, look at Sophos instead. Trend Micro Vision One – Overall Rating: 3.9/5 MITRE scores: 3.5/5 Customer support: 3.4/5 Trend Micro Vision One is a unified security platform for businesses of all sizes. With features like remediation suggestions and customized playbooks, it’s designed to protect the entire security infrastructure. Trend Micro has been consistently building its security business for years, and Vision One is proof of that, with functionality for both large enterprises and SMBs. Similar to CrowdStrike, Vision One is designed to cover multiple facets of business security. Free trial lasts a month Cons Incident prioritization capabilities are unclear No official product demo Free trial: 30 days Key Features Attack surface discovery: Vision One tracks down unknown assets and attack surfaces that aren’t yet scanned and protected. Vulnerability management: The platform shows admins data like commonly exploited vulnerabilities and legacy operating systems being used. Risk scores: Trend Micro uses global threat intelligence sources to help determine which vulnerabilities are the most critical and should be fixed first. Variety of response options: Vision One can isolate endpoints, terminate processes, send threats to a sandbox, and force users to reset their passwords. Screenshot Alternatives Vision One is a great solution for teams that want a comprehensive security platform, but a couple of its endpoint security features are unclear, including device controls and incident triage. If these are big priorities for you, consider Cybereason instead. Cybereason – MITRE scores: 5/5 Customer support: 3.8/5 Cybereason is an enterprise-grade detection and response platform ideal for larger teams, though SMBs with a sizable budget can certainly benefit from it, too. One of its differentiating features is the MalOp, or malicious operation, a method of tracking individual threats and all associated data. If you’re looking for a strong managed defense platform similar to CrowdStrike, Cybereason is a great choice, particularly for threat visualization. Available as a managed service Excellent MITRE scores in recent testing Cons No free trial Free demo: Contact to schedule Key Features Endpoint control: Within a single interface, admins can set rules for specific endpoints based on their business’s security policies. Threat intelligence: Cybereason compares multiple threat feeds using machine learning-based analysis to determine which feeds are most helpful. Remediation assistance: The platform shows admins which tools threat actors use and helps them quickly block threats and isolate malicious files. Integrations: Technology partners of the Cybereason Defense Platform include Okta, Proofpoint, Fortinet, and Palo Alto. Screenshot Alternatives Cybereason is a strong choice for large enterprises and security teams that want to truly visualize the connections between different events. However, it’s not the best choice for small teams; consider Bitdefender instead if your business needs something a bit simpler. Bitdefender GravityZone – MITRE scores: 3.8/5 Customer support: 3.4/5 Bitdefender GravityZone is a multi-purpose security platform for both small businesses and enterprises. You can choose your GravityZone package based on need; the most basic plan truly is an SMB solution, with features like web control and filtering. However, the enterprise option offers plenty for large and experienced teams, like correlation across endpoints and response suggestions. Like CrowdStrike Falcon, GravityZone provides pricing for small teams. Transparent pricing for very small teams Month-long free trial No support email or live chat available No native incident triage or threat intel Pricing More than 100 devices: Contact for quote Free trial: One month Key Features Ransomware mitigation: When GravityZone detects strange encryption procedures, it creates tamper-proof file copies so the data won’t be lost. Risk management: Bitdefender assigns risk scores to individual threats and prioritizes misconfigurations and behaviors depending on criticality. Sandboxing: GravityZone can automatically send suspicious files or code to the Sandbox Analyzer, determining whether it’s malicious. Single pane of glass: GravityZone combines the whole Business Security platform into one management console, so your admins can manage everything from one location. Screenshot Alternatives GravityZone is a great endpoint security solution for businesses but is unavailable as a managed service. If your business needs an MDR platform, look at Trend Micro instead. Sophos Intercept X – MITRE scores: 4/5 Customer support: 4.3/5 Sophos is an extremely popular network security and EDR provider with customers. It offers tools like application and peripheral device control for managing endpoints. Renowned for its usability, Sophos is a strong solution for SMBs and less experienced teams, though it provides features like data loss prevention for larger companies. While CrowdStrike is a highly advanced platform, Sophos is ideal for teams that need a basic but strong EDR foundation. Managed service option through Sophos MDR User interface is popular with customers Cons Free trial: 30 days Key Features Prioritized detection: Intercept X uses artificial intelligence to prioritize which threats to detect. Web protection: Sophos examines web pages and data like IP addresses and blocks user access to malicious sites when needed. Behavioral analysis: The platform works over a period of time to gather process, registry, and file event data and determine threats versus normal activity. File integrity monitoring: Sophos protects Windows servers by identifying changes to the critical files on the servers. Screenshot Alternatives Sophos is an outstanding solution for smaller teams and more basic EDR requirements, but it might not have enough advanced features for large enterprises. If your team needs more functionality, consider Palo Alto instead. If you’re working to protect your entire business network, learn more about different types of network security solutions , like virtual private networks and firewalls. Symantec Endpoint Security – MITRE scores: 2/5 Customer support: 2.6/5 Symantec, recently acquired by Broadcom, is an EDR solution offering broad endpoint and server management. Features include custom detection rules and suggestions for remediation. Symantec’s security capabilities extend to multiple operating systems and mobile devices. It’s designed to protect data centers, hybrid infrastructures, and storage solutions like cloud buckets and network-attached storage. Like CrowdStrike, Symantec offers managed security services. Multiple training videos available Cons Pricing Key Features Device controls: Security teams can develop rules to control peripheral devices like USBs connecting to endpoints within the infrastructure. Attack visibility: Symantec EDR shows you the attack chain of events during an incident, which you can sort chronologically and then perform remediations. Managing assets: Part of the endpoint management solution, asset relationships and software license management help teams better visualize their organization’s hardware and software. Custom rules: You can add your own incident detection rules to find threats that Symantec’s existing rules don’t already cover. Screenshot Alternatives While Symantec is a strong endpoint security solution, some customers complained about customer support responsiveness after the Broadcom acquisition. Consider Sophos if you’re looking for a solution with high customer service reviews. 5 Key Features of CrowdStrike Competitors Endpoint security platforms like CrowdStrike Falcon typically offer features like device control, incident isolation, suggestions for remediation, threat intelligence, and mobile device support. Device Controls Endpoint security platforms typically offer device controls so teams can block or isolate devices that are seeing — or causing — security problems. This could be a strain of malware on a laptop or a mobile application trying to gain unauthorized access to a service. Admins can isolate the device so any threat won’t spread or block certain malicious processes. Incident Quarantine Often, threat actors use lateral movement to travel through IT environments, but they can do that because of insufficient permissions and the connection points between devices and applications. Endpoint security solutions should allow admins to quarantine incidents, or whole devices, so threats like malware can’t spread further. Remediation Recommendations Endpoint detection and response often include suggestions for remediating threats. A management console might provide threat data like affected applications and then give a listed process for mitigating the threat, like quarantining it or sending it to a sandbox. These suggestions are helpful for security admins because they’re based on data that the EDR solution has already compiled, and the automation also saves the admins manual work. Threat Intelligence Endpoint security vendors like CrowdStrike often integrate with popular threat intelligence feeds or perform their own threat research. Security platforms like EDR and XDR need to have accurate sources of threat data. These platforms will be better prepared to combat threats with a strong understanding of them and their associated indicators of compromise. Support for Mobile Operating Systems Ideally, endpoint security suites like CrowdStrike should cover mobile devices like phones, not just laptops and servers. Mobile phones can be just as much of a threat to enterprise security as computers, especially if they’re connected to a business network or are used to store sensitive data. Often, security platforms like EDR cover Android and iOS. Flaws in mobile devices aren’t the only threats to business networks. Read more about major network security threats , including malware and denial of service, in our guide. How I Evaluated CrowdStrike’s Main Competitors To analyze the best alternatives to CrowdStrike Falcon, the vendor’s main platform, I created a product scoring rubric that analyzed solutions in the endpoint security, EDR, and XDR spaces. The rubric included six major categories that buyers look for in endpoint security solutions. Each category had its own weight, and each also included multiple subcriteria. How well each security product met the subcriteria and their weighting contributed to their final score. Evaluation Criteria I started with core endpoint security features, like device controls, when creating the rubric. Then I looked at usability and administrative features, like documentation and training videos. Next, I considered pricing, which included free trials, and advanced features, such as threat hunting. I also scored the products based on vendors’ MITRE Evaluation scores, which come from independent tests. Finally, I looked at customer support, including the availability of demos. Core features (25%): This category included the most important endpoint security features, like vulnerability management, remediation suggestions, and device control. Ease of use and administration (20%): I evaluated usability features like documentation, APIs, and a single management console. Criterion winner: Multiple winners Pricing (15%): I looked at the availability of pricing information, including from resellers, and also evaluated free trials. Advanced features (15%): These included nice-to-have capabilities like threat hunting and rogue device discovery, which are particularly helpful for enterprises. MITRE scores (15%): I scored the products based on their MITRE Evaluation results, which indicate how well they can actually protect computer systems. Criterion winner: Multiple winners Customer support (10%): I considered customer support channels, like phone and email, as well as product demo availability. Is CrowdStrike Better Than Competitors? The top endpoint security and EDR platforms excel in different areas, including detection, protection, threat intelligence, and research. CrowdStrike is particularly renowned for its defense capabilities. However, multiple other providers do well in threat protection — just look for signs like strong independent testing scores; these show that vendors can actually use the features they claim to offer. Who Is CrowdStrike’s Biggest Competitor? CrowdStrike has plenty of competitors, but the most notable one is probably Palo Alto Networks, one of the world’s best detection and response providers. It offers similar features and earns very comparable independent testing scores. Palo Alto actually received the best score in the most recent MITRE ATT&CK evaluations and was the only vendor to stop all tests perfectly. What’s the Difference Between Antivirus, Endpoint Protection Platforms & EDR? CrowdStrike and its competitors all offer features in the antivirus, endpoint protection, and EDR families. However, the three have distinctions, even if they’re typically combined on CrowdStrike Falcon and other platforms. Antivirus solutions are mainly concerned with protecting computer systems from viruses and malware. Endpoint protection platforms prevent threats on devices like laptops, and EDR platforms combine preventative features with direct response. Learn more about the differences between antivirus, endpoint protection platforms, and endpoint detection and response in our guide to the three. Bottom Line: Choosing An Alternative to CrowdStrike Whether you’re looking for your business’s first EDR platform or trying to replace an existing instance of CrowdStrike Falcon, consider the key features your team needs when evaluating competitors. Falcon is renowned for its threat prevention capabilities, but other solutions can provide that, too. Look for strong independent testing scores that indicate actual ability, but consider administrative and support features that affect usability, too. Is your business specifically looking for a managed endpoint security solution? Check out our guide to the best managed detection and response solutions , including Alert Logic and SentinelOne. Get the Free Cybersecurity Newsletter Strengthen your organization’s IT security defenses by keeping up to date on the latest cybersecurity news, solutions, and best practices. Delivered every Monday, Tuesday and Thursday Email Address By signing up to receive our newsletter, you agree to our Terms of Use and Privacy Policy. You can unsubscribe at any time. Subscribe
Cybereason Frequently Asked Questions (FAQ)
When was Cybereason founded?
Cybereason was founded in 2012.
Where is Cybereason's headquarters?
Cybereason's headquarters is located at 200 Berkeley Street, Boston.
What is Cybereason's latest funding round?
Cybereason's latest funding round is Valuation Change.
How much did Cybereason raise?
Cybereason raised a total of $813.62M.
Who are the investors of Cybereason?
Investors of Cybereason include SoftBank, Google Cloud Platform, Neuberger Berman, Liberty Strategic Capital, Irving Investors and 6 more.
Who are Cybereason's competitors?
Competitors of Cybereason include BlueVoyant, HarfangLab, Absolute Software, Minerva Labs, Expel and 7 more.
What products does Cybereason offer?
Cybereason's products include Cybereason XDR and 3 more.
Loading...
Compare Cybereason to Competitors
eSentire focuses on managed detection and response services in the cybersecurity industry. The company offers a range of services including exposure management services, managed detection and response, and digital forensics and incident response, all aimed at identifying security gaps, improving threat detection, and providing rapid response to cyber threats. It primarily serves various sectors including the insurance, construction, finance, legal, manufacturing, private equity, healthcare, and retail industries. It was founded in 2001 and is based in Waterloo, Canada.
Cerebra operates as a software products company focusing on the design and development of cybersecurity technologies. The company offers a range of products including a cybersecurity awareness platform, a multi-factor authentication solution, a phishing simulation solution, and an enterprise messaging gateway. It aims to protect organizations from cyber threats and enhance their cybersecurity awareness. Cerebra was founded in 2020 and is based in Riyadh, Saudi Arabia.

Sophos provides information technology services. The company offers security and data protection, data loss prevention, patch assessment, full-disk encryption, firewall, intrusion prevention system, mobile device management, wireless security, and network access control. It offers its solutions in a wide range of industries such as education, healthcare, manufacturing, retail, and more. The company was founded in 1985 and is based in Abingdon, United Kingdom.
The VP Techno Labs International facilitates cybersecurity solutions. The company offers cybersecurity solutions, using its proprietary Triple Shield DRE methodologies, to protect businesses from cyber threats that could impact their revenue and reputation. The company primarily serves a wide range of sectors including the pharmaceutical, healthcare, hospitality, automotive, and retail industries. It was founded in 2019 and is based in India.

Expel operates as a security operations company and specializes in managed detection and response (MDR) within the cybersecurity industry. The company offers various services such as 24/7 monitoring, threat detection, incident response, and security infrastructure optimization. Expel was formerly known as The Concern. It was founded in 2016 and is based in Herndon, Virginia.

Darktrace specializes in cyber security, leveraging self-learning AI technology within the cyber security industry. The company offers a suite of solutions that provide threat detection, visibility, and automated response to cyber-attacks across various digital environments. It was founded in 2013 and is based in Cambridge, United Kingdom.
Loading...