HYPR
Founded Year
2014Stage
Private Equity | AliveTotal Raised
$123.15MLast Raised
$30M | 4 mos agoMosaic Score The Mosaic Score is an algorithm that measures the overall financial health and market potential of private companies.
+28 points in the past 30 days
About HYPR
HYPR specializes in identity security and passwordless authentication solutions within the cybersecurity industry. The company offers an identity assurance platform that includes passwordless multi-factor authentication, risk policy orchestration, and identity verification services. HYPR's solutions cater to various sectors, including financial services, critical infrastructure, and retail, aiming to enhance security and user experience. It was founded in 2014 and is based in New York, New York.
Loading...
ESPs containing HYPR
The ESP matrix leverages data and analyst insight to identify and rank leading companies in a given technology landscape.
The passwordless authentication tools market offers solutions that eliminate passwords to mitigate the risk of cybersecurity incidents caused by compromised credentials. This market offers organizations a more secure access posture and can help combat phishing and data breaches at scale. At the same time, these solutions aim to improve login experiences for employees and customers by offering a mo…
HYPR named as Outperformer among 15 other companies, including Okta, Yubico, and OpenText.
HYPR's Products & Differentiators
True Passwordless MFA
HYPR solution for workforce
Loading...
Research containing HYPR
Get data-driven expert analysis from the CB Insights Intelligence Unit.
CB Insights Intelligence Analysts have mentioned HYPR in 5 CB Insights research briefs, most recently on Feb 20, 2024.

Feb 20, 2024
The hardware security market map
Nov 3, 2023
The endpoint security market mapExpert Collections containing HYPR
Expert Collections are analyst-curated lists that highlight the companies you need to know in the most important technology spaces.
HYPR is included in 6 Expert Collections, including Regtech.
Regtech
1,921 items
Technology that addresses regulatory challenges and facilitates the delivery of compliance requirements. Regulatory technology helps companies and regulators address challenges ranging from compliance (e.g. AML/KYC) automation and improved risk management.
Payments
3,034 items
Companies in this collection provide technology that enables consumers and businesses to pay, collect, automate, and settle transfers of currency, both online and at the physical point-of-sale.
Cybersecurity
9,489 items
These companies protect organizations from digital threats.
Fintech
9,295 items
Companies and startups in this collection provide technology to streamline, improve, and transform financial services, products, and operations for individuals and businesses.
Fintech 100
500 items
250 of the most promising private companies applying a mix of software and technology to transform the financial services industry.
Digital ID In Fintech
268 items
For this analysis, we looked at digital ID companies working in or with near-term potential to work in fintech applications. Startups here are enabling fintech companies to verify government documents, authenticate with biometrics, and combat fraudulent logins.
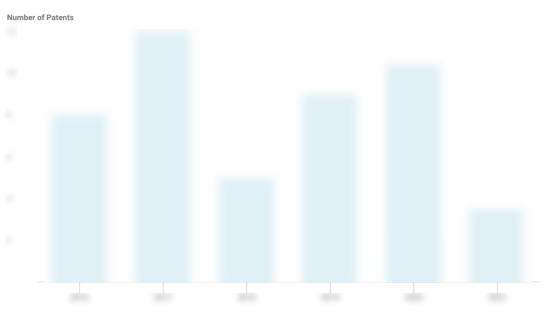
HYPR Patents
HYPR has filed 25 patents.
The 3 most popular patent topics include:
- computer security
- cryptographic protocols
- cryptography
Application Date | Grant Date | Title | Related Topics | Status |
|---|---|---|---|---|
5/9/2022 | 9/17/2024 | Cryptocurrencies, Payment systems, Digital currencies, Digital currency exchange, Alternative currencies | Grant |
Application Date | 5/9/2022 |
|---|---|
Grant Date | 9/17/2024 |
Title | |
Related Topics | Cryptocurrencies, Payment systems, Digital currencies, Digital currency exchange, Alternative currencies |
Status | Grant |
Latest HYPR News
Aug 15, 2024
Security Boulevard Community Chats Webinars Library Going Passwordless: 6 Tips to Navigate Passkey Adoption By now, most of us realize that passkeys and passwordless authentication beat passwords in nearly every way — they’re more secure, resist phishing and theft, and eliminate the need to remember and type in an ever-growing string of characters. Despite this, most organizations still rely on password-based authentication methods. Transitioning to passwordless authentication offers a far more secure and user-friendly experience, but making the switch can seem daunting. In fact, the most recent Passwordless Identity Assurance survey found that nearly one third (31%) of organizations name implementing passkeys as a primary identity security challenge. Technical integration is only one aspect. For many organizations, rolling it out to users and getting them to use it can be the thornier part. Understanding User Adoption User resistance to an unfamiliar technology can be a hurdle in transitioning to passwordless. It’s critical to take a phased, change management approach, including pilot programs and early adopter groups. Clear communication about the benefits of passkey systems, referencing successful case studies, and industry best practices, helps allay user skepticism and increase acceptance. User-centric design and understanding the psychology of habit formation are essential to achieve widespread adoption. User experience greatly impacts a passwordless initiative — balancing security and convenience is key. Consider and address your varying use cases, potential accessibility issues, and technical challenges, such as legacy systems. As Director of Customer Excellence at HYPR, I’ve worked with many customers during their passwordless transition. As someone with even more years in IAM and customer experience in general, I’ve seen and heard many tech rollout tales. Here are some of the top tips to help your organization navigate passkey adoption effectively. Best Practices for Passkey Adoption 1. Map Out Use Cases Different user groups within an organization may have varying needs, both in their job function and as individuals. When it comes to passkey adoption, one size doesn’t fit all. Multiple passwordless options may be required. Begin by getting a full picture of your current login methods. Identify priority login systems and stakeholders. Do you haveremote or hybrid employees?. What IdPs, devices, browsers and operating systems are being used? Consider non-employees like contractors, business partners, or volunteers — when and how do they log in? For users who travel extensively, note any special authentication requirements. PRO TIP: Identify any applications, systems, or tools with additional authentication controls due to sensitive data. Evaluate specific user accounts, like IT administrators, with higher security needs. 2. Identify and Plan for Legacy Systems and Other Challenges Passwordless deployments can be hindered by legacy systems, technical and usability concerns and under preparedness for the reliance on secondary devices. Look at the legacy applications in your tech stack, how they are used, and their current authentication methods. Will your passwordless solution integrate with them? If system updates or configurations are required for compatibility, make sure to get leadership buy-in during the planning stage. Addressing technical and usability concerns requires capturing all unique workstream requirements and considering business-specific constraints. For example, customer-facing roles may have different constraints than back-office roles or a manufacturing floor. Users that travel may require offline authentication options. PRO TIP: The reliance on secondary devices makes it critical to be ready with secure recovery and backup options. 3. Strategic Planning for Rollout Thorough planning and secure process design are critical for successful rollout. Authentication is a critical path product — ensure you’re prepared. Establish timelines, set roll-out stages, and develop communication plans. Conduct a pilot test with a small group to help identify and address potential issues before roll out. Take the roll out in stages too, beginning with a first adopter group. This approach allows for fine-tuning the system and ensuring a smoother transition for the entire organization. Ideally, the group will include both technically-minded people as well as those less comfortable with technology. Your early adopters should represent a cross-section of use cases, especially privileged users or other groups with specific security requirements. The sequence and timing of roll out will depend on your unique environment and business, but make sure senior leadership is part of the earliest stages — a top-down approach significantly helps end-user buy-in and speed passkey adoption. Communication during all stages is critical to both educate and preempt objections. Concerns about biometric data usage, for example, can be mitigated through educational campaigns that clarify how such data is stored and protected. PRO TIP: Consider aligning your password policy with your improved security strategy by enforcing complex passwords in line with guidance from CISA and PCI DSS 4.0 requirements . Your users will look forward to the ease of passwordless authentication. 4. Clear Communication and Guidance Effective communication and guidance are essential for facilitating passkey adoption. Clear, concise, and user-friendly documentation can help users understand and adapt to new authentication methods. Early adopters can provide invaluable feedback to improve documentation and identify fringe use cases and outlier scenarios. User adoption relies on awareness of the improvements passwordless authentication offers over traditional methods. The FIDO Alliance provides some helpful communication recommendations in their Design Guidelines. Explain that you are replacing passwords with stronger, phishing-resistant authentication. Don’t get hung up on terminology – use what works best for your users. For example, one of our customers used the term “non-shareable credentials” instead of passwordless authentication or passkeys as that resonated better with their workforce. Provide training on new login flows, highlighting speed, ease-of-use and security. Use multiple touchpoints, such as town halls, training videos, and cheat sheets. Include guidelines for troubleshooting issues like lost devices and keep stakeholders updated throughout the transition. Importantly, solicit user feedback and be prepared to adjust communication materials if needed. Example user communication courtesy of the FIDO Alliance 5. User Onboarding and Support Plan for supporting your users when the new system goes live. Make sure you take into account the needs of users in different time zones or those who travel frequently. Train your help desk to educate as well as troubleshoot. Ensure that support resources are readily available to address any issues that arise. Monitor KPIs like login times, call volume and ticket metrics pre vs post-implementation. PRO TIP: Create a promotion or contest, with prizes. Use gift incentives, swag or giveaways to first or all enrollees. 6. Choose the Right Passwordless Solution All of the previous steps depend upon you selecting the right passwordless provider for your environment, user population and use cases. The optimal solution removes adoption obstacles, balancing hardened security with maximized convenience and quick deployment. If you’re reading this, you’ve likely decided that a solution based on FIDO Certified passkeys is the best approach, but there are a wide range of options within this category. Assess vendor offerings based on cryptography standards, biometric and device support, scalability, customer success rate and implementation timeframe. Ease of integration with existing web/IT infrastructure is critical. 💡12 Considerations for Assessing a Passkey Solution — Download the Guide PRO TIP: Don’t forget that secondary authentication processes and situations — registration, re-registration, lost and stolen devices — must also be protected. Look at your provider’s entire set of identity security capabilities — do they provide identity proofing technologies and other critical identity security controls? HYPR Is Your Passkey Adoption Partner Companies need an identity security partner with expertise in change management and a solution that provides flexibility along with the controls enterprises require. HYPR has been helping companies implement passkeys and passwordless authentication for more than a decade. This includes a top U.S. bank with the largest workforce FIDO implementation in the world. HYPR’s leading passwordless MFA solution , HYPR Authenticate, eliminates shared credentials while providing a friction-free user experience. It offers a range of authenticator options, including our award-winning passwordless app, and works everywhere, whether in-office or remote, online or off. HYPR Authenticate is the foundation of our Identity Assurance Platform , which combiness phishing-resistant authentication, adaptive risk mitigation, and automated identity proofing and verification to secure the entire identity lifecycle. HYPR Integrates with your current systems, IdPs, SSOs and applications to unify authentication across the business. *** This is a Security Bloggers Network syndicated blog from HYPR Blog authored by Darrin Ingram . Read the original post at: https://blog.hypr.com/tips-to-navigate-passkey-adoption
HYPR Frequently Asked Questions (FAQ)
When was HYPR founded?
HYPR was founded in 2014.
Where is HYPR's headquarters?
HYPR's headquarters is located at 1001 Avenue of the Americas, New York.
What is HYPR's latest funding round?
HYPR's latest funding round is Private Equity.
How much did HYPR raise?
HYPR raised a total of $123.15M.
Who are the investors of HYPR?
Investors of HYPR include Silver Lake, RRE Ventures, Comcast Ventures, .406 Ventures, Advent International and 12 more.
Who are HYPR's competitors?
Competitors of HYPR include Keyless, Axiad, Wink, BioCatch, Sentry Enterprises and 7 more.
What products does HYPR offer?
HYPR's products include True Passwordless MFA and 1 more.
Loading...
Compare HYPR to Competitors
BIOWATCH develops a biometric recognition system integrated into any wearable device for secure authentication, mobile payment protection, and smart device interaction. It enables users to unlock a car, access an office, log in to the internet, purchase goods and services, and sign contracts and digital documents. The company was founded in 2015 and is based in Lausanne, Switzerland.

Socure focuses on digital identity verification and fraud prediction, operating within the technology and financial services sectors. The company offers a platform that uses artificial intelligence (AI) and machine learning (ML) to verify identities in real-time, analyzing various elements such as email, phone, address, and device risk. This service is primarily used by industries such as financial services, government, gaming, healthcare, telecom, and e-commerce. It was founded in 2012 and is based in Incline Village, Nevada.
Tactical Information Systems provides complete identity solutions that meet the needs of governments, law enforcement, border security and identity communities. BeehiveID is face recognition software for identity authentication & verification.

Transmit Security focuses on providing cloud-native customer identity and access management (CIAM) services. The company offers a range of identity services including identity orchestration, detection and response, identity management, identity verification, authentication services, and data validation. These services are designed to consolidate identity stacks, centralize decision-making, automate customer journeys, monitor and analyze risk signals, and more. It was founded in 2014 and is based in Boston, Massachusetts.
InCights Mobile Solutions is a developer and provider of voice biometrics software and delivery systems. The company's vision is to establish Voice biometrics as a de-facto standard for remote authentication over telephony and other online channels.
Nok Nok Labs is a company that focuses on providing next-level passwordless multi-factor authentication solutions in the digital security industry. The company offers services such as passwordless authentication, secure payments, and compliance, aiming to replace weak legacy login methods with modern, secure, and frictionless experiences. Nok Nok Labs primarily serves sectors such as the government, e-commerce, financial services, and mobile network operators. It was founded in 2012 and is based in Palo Alto, California.
Loading...