Quantum computing could break the encryption used today to secure everything from emails to bank payments, but new encryption approaches will help. We look at what post-quantum cryptography is and what companies need to think about before implementing it.
The internet isn’t ready for quantum computing.
Quantum computers process information in a fundamentally different way than their classical counterparts. Eventually, they will be able to quickly crack many of today’s public-key encryption methods — a form of encryption that underpins the security of emails, payments, digital certificates for proving the authenticity of websites, and more.
The stakes are high. Any organization relying on current methods for public-key encryption — including banks, shops, and hospitals — would be vulnerable to being hacked, making even the worst data breaches of recent years pale in comparison.
Though this “quantum time bomb” will likely not go off for a while, the risk is quickly becoming a high priority given the accelerating pace of quantum computing advances. Transitioning to new encryption protocols could take years — or even decades — to complete.
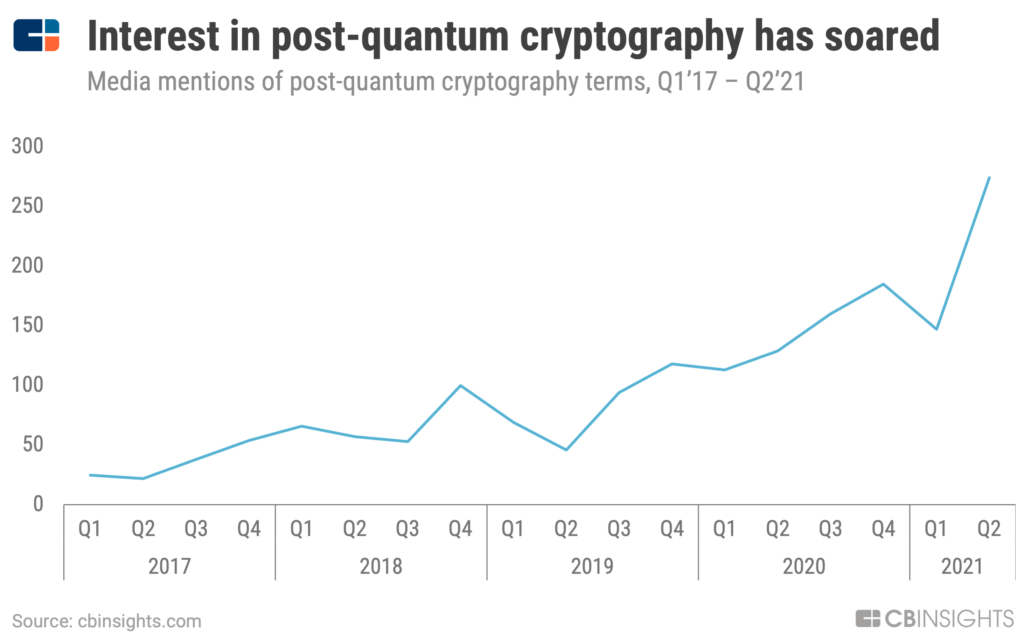
However, new public-key encryption techniques that can defend against this quantum threat are already emerging. Known collectively as “post-quantum cryptography (PQC),” these techniques employ encryption algorithms that even a quantum computer couldn’t easily crack, and are sometimes described as being “quantum-resistant” or “quantum-safe.” Interest in the PQC space is rising quickly, with media mentions skyrocketing in 2021.
The stage is set for a race between the adoption of post-quantum cryptography and the development of powerful quantum computers. Post-quantum cryptography has a head start, but quantum computing advances are accelerating.
Funding is pouring into quantum computing companies like PsiQuantum, Rigetti, Cold Quanta, and many others hoping to disrupt major industries. Google, Microsoft, Amazon, IBM, Honeywell, and other big corporations have placed enormous bets in the space. 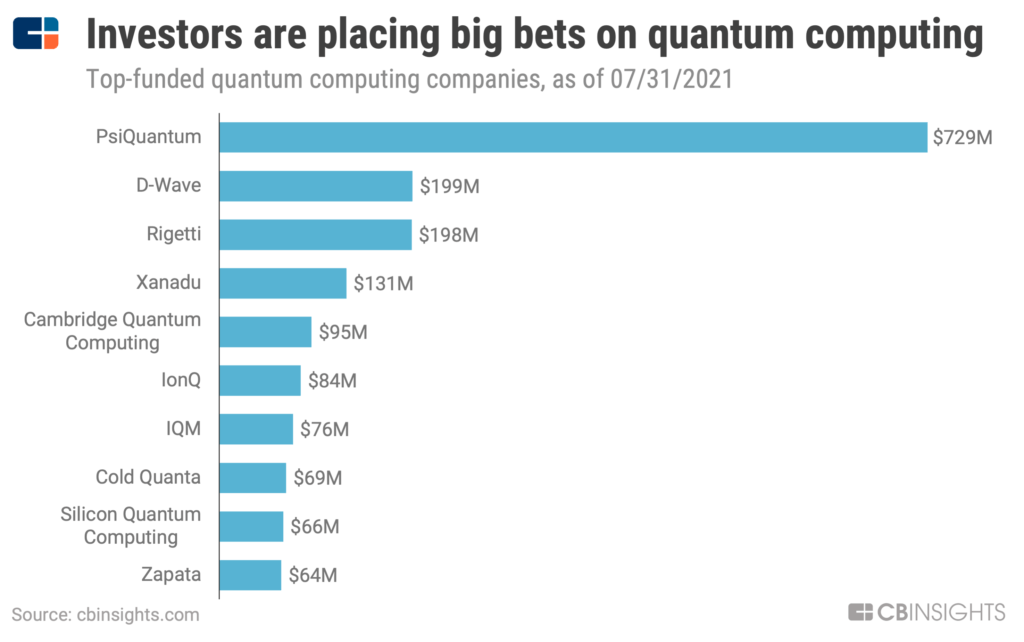
All it takes is for one quantum computing approach to succeed for much of the internet to no longer be considered secure. In this report, we break down how post-quantum cryptography works, who the key players are, what companies should consider for adopting PQC, and more.
Table of contents
- What is post-quantum cryptography?
- Who are the post-quantum cryptography players?
- What should a company consider for adopting post-quantum cryptography?
- What’s ahead for post-quantum cryptography?
Learn how quantum computers work, the industry landscape, and the tech’s applications beyond cybersecurity in this deep dive report. CB Insights clients can track quantum computing companies using our Quantum Tech Expert Collection.
Track all the quantum tech companies in this report and many more on our platform
Companies working on quantum computing, quantum communication, quantum sensors, and more.
Track Quantum Tech Companies
What is post-quantum cryptography?
Post-quantum cryptography typically refers to public-key cryptography methods that are designed to be resistant to quantum computer-based attacks.
How does public-key cryptography work?
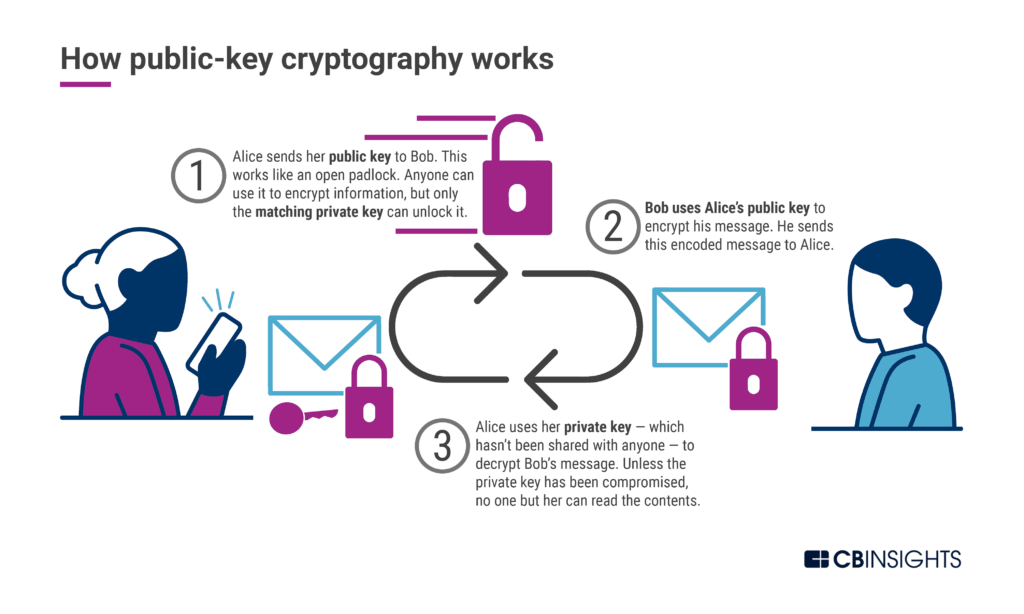
Public-key cryptography, also known as “asymmetric cryptography,” lets multiple parties communicate securely over an open network without having already agreed on an “encryption key” — a code that can be used to scramble information and make it meaningless to observers without the right key.
Public-key encryption allows someone to send out a public key that can encrypt information but cannot decode it. Anyone can see the public key and use it to encode messages, but only the person who has the matching private key can decrypt it. The public key functions like an open padlock — anyone who finds it can close it to secure something, but only the person who has the padlock’s key can open it again.
This means that different parties can pass messages over the internet that only the recipient can read. Today, quantum-vulnerable methods for public-key cryptography — such as RSA encryption — are used widely and underpin the security of lots of online activity, from messages to payments to logging into a website.
Why do quantum computers threaten today’s public-key cryptography?
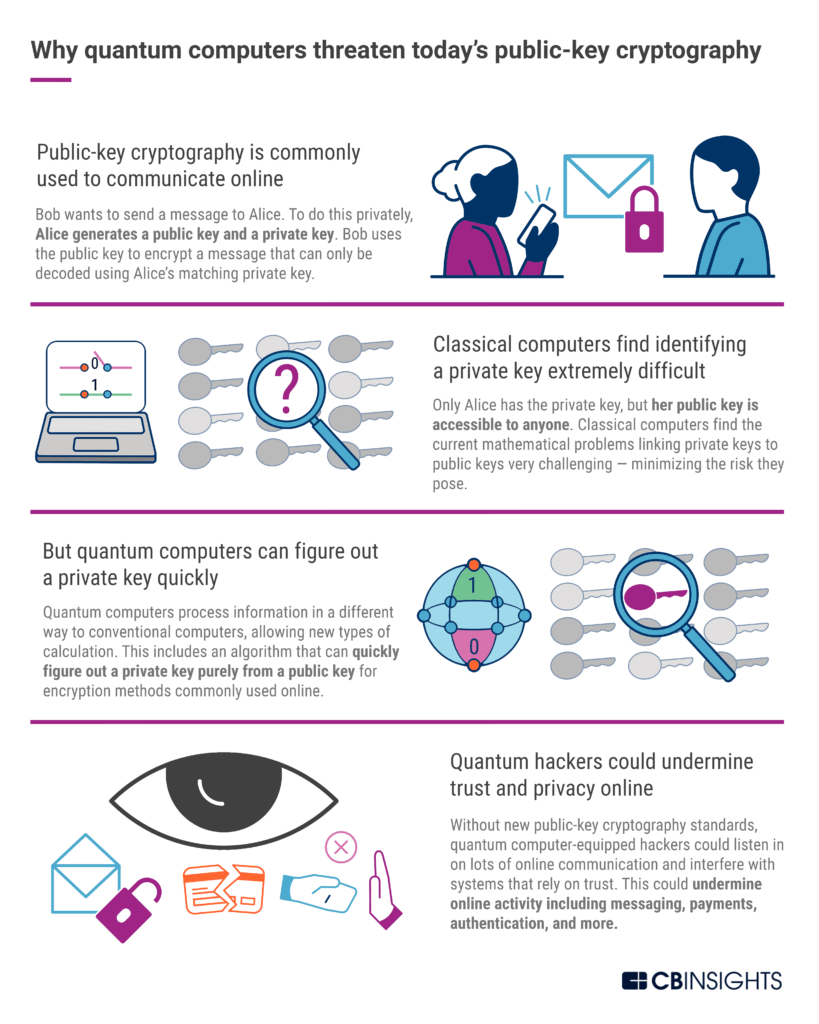
Public keys and private keys are mathematically linked. Today’s methods for public-key cryptography rely on mathematical problems that conventional computers find extremely difficult, such as finding the prime factors of a very large number.
But quantum computers process information in a way that allows them to do some types of calculations that classical computers can’t.
This includes Shor’s algorithm, which provides a highly efficient way to tackle the very mathematical challenges currently keeping much of our public-key-based online communications private. If Shor’s algorithm was being run by a powerful quantum computer, then most of today’s public-key cryptography approaches wouldn’t hold up.
This is where post-quantum cryptography comes in.
How does post-quantum cryptography defend against quantum computers?
PQC links private keys to public keys without using problems that quantum computers can easily solve. In other words, it aims to deliver the benefits of today’s public-key encryption without the vulnerability to quantum hacking.
Approaches to PQC include building encryption around mathematical “structures” called lattices, using systems purely based upon code, solving complicated problems involving multiple variables, and much more.
Who are the post-quantum cryptography players?
Post-quantum cryptography is attracting attention from organizations including governments and affiliated agencies, corporations, and startups.
The National Institute of Standards and Technology (NIST), a US-based standard-setting body, is a central player in the space. It’s currently evaluating leading post-quantum cryptography candidates and is due to announce new standards for public-key encryption within the next year or so.
But activity in the sector is picking up even as companies wait for NIST to complete its process:
- Major tech players including Microsoft and IBM are developing their own candidates for post-quantum cryptography algorithms.
- Amazon’s AWS cloud platform has begun to offer support for some PQC protocols.
- Intel is working on ways to bring PQC to low-powered IoT devices.
With a lot of money riding on the security of their transactions, big financial companies are also making early moves. For example, Mastercard recently launched a new wireless payments protocol that it claims is quantum-safe. Meanwhile, its rival VISA has published multiple papers exploring how PQC could affect payments. JPMorgan is reportedly already combing through its systems to identify which data to prioritize for a quantum-safe revamp.
Meanwhile, a growing number of startups are looking to gain an early-mover advantage and position themselves for a coming surge in demand. ISARA, PQShield, and Post-Quantum are among the most well-funded companies in the space, with all 3 aiming to help enterprises and governments transition to post-quantum cryptography systems.
Other startups are working on niche quantum-resistant applications, such as more secure blockchains (Cellframe), protecting IoT systems (AgilePQ), and encrypted telehealth platforms (Cyph).
CB Insights clients can check out the full quantum tech market map here and can see many more post-quantum cryptography companies in our Quantum Tech Expert Collection.
What should a company consider for adopting post-quantum cryptography?
Pretty much every company will eventually move to some form of post-quantum cryptography, but when and how will be key considerations.
What cybersecurity threat do quantum computers pose to companies?
Most of what a company does online could be impacted by the onset of powerful quantum computers. This is because public-key cryptography plays a role in all sorts of things, including:
- Sending messages online
- Facilitating online payments
- Logging into websites
- Blockchain applications
- Accessing data stored online
- Securing IoT devices
This means that a company that was not protected against a quantum computer-backed hack would not be able to meaningfully assure customers that its systems were secure once a powerful quantum computer emerged.
When will companies need to adopt post-quantum cryptography?
A number of cybersecurity players, including researchers working for NIST and the UK’s National Cyber Security Centre (NCSC), are recommending that enterprises already begin laying the groundwork for migrating to post-quantum cryptography and then move quickly to implement new encryption approaches when PQC standards are announced.
But some in the space also caution against actually committing to a particular PQC approach until standards have been set within the coming year or so.
The quantum threat won’t materialize overnight, but transitioning to post-quantum cryptography will take a long time
Though it is widely accepted that quantum computers will eventually render a lot of today’s public-key encryption obsolete, the actual timeline is impossible to predict. Most estimates fall within the range of 10-20 years, but the threshold could be passed much earlier if quantum computer producers make an unforeseen breakthrough.
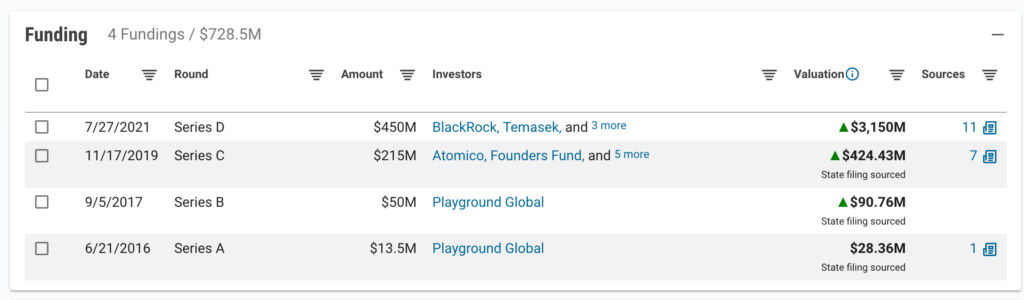
For instance, PsiQuantum, the most well-funded quantum computing startup in the world, claims that it will have a 1M qubit quantum computer within just a few years. (Qubits are what quantum computers use to conduct calculations. Read about how they work in this explainer.) If achieved, this would signal that the tech is evolving much faster than many thought possible.
Quantum computer maker PsiQuantum raised a $450M mega-round at a $3B+ valuation in July.
In any event, transitioning to post-quantum cryptography is expected to take a decade or more, driving a sense of urgency to upgrade systems as soon as possible so that companies aren’t caught off guard when capable quantum computers emerge.
Data harvested now can be decrypted later
Data encrypted with quantum-vulnerable algorithms can be intercepted now and stored for a time when powerful quantum computers exist. This is a key concern for governments wanting to guard secrets, but companies dealing with sensitive information — such as key IP or some types of personal information — may also need to develop a strategy to counter this drawn-out hack.
Implementing PQC for high-priority data will solve this issue going forward, but nothing can be done for information that has already been squirreled away.
Standards haven’t arrived yet, but preparations can already begin
Many companies are waiting until NIST announces its post-quantum cryptography standards before making the leap. This approach reduces the likelihood of running into interoperability issues and will help ensure that the PQC approach being deployed actually works as intended.
However, enterprises can still make moves to start preparing for PQC. This includes:
- figuring out how they are currently using public-key cryptography
- understanding the requirements and constraints of their systems (issues like data latency needs, hardware specs, and legal compliance could all influence a transition to PQC)
- identifying what data is especially sensitive
What are the barriers to the adoption of post-quantum cryptography?
Public-key cryptography is used everywhere; updating it will be challenging
Transitioning to post-quantum cryptography will be difficult. Public-key cryptography is used in lots of different ways for a broad range of purposes, from passwords to digital signatures for websites to facilitating other types of encryption.
Successfully updating all of these instances is unlikely to be as simple as a software update. Depending on the circumstance, it may require new hardware, installing infrastructure, redrafting security protocols, or even renegotiating contracts with external partners.
Given this complexity, a major cybersecurity risk going forward is that some companies may be tempted to not bother upgrading their systems.
Post-quantum cryptography approaches vary widely in their advantages and constraints; expect different standards for different applications
In general, post-quantum cryptography will be more taxing on computers than what is currently used, but some will need more power than others and different approaches will offer varying risk profiles.
Given the broad set of tasks that public-key encryption is used for, it’s possible that NIST will recommend different PQC standards depending on the use case. For example, one approach may be recommended for low-powered IoT devices not carrying highly sensitive data, while another may be recommended for tasks like facilitating online data storage.
How does quantum key distribution relate to post-quantum cryptography?
Another encryption technology to keep an eye on is “quantum key distribution” (QKD), sometimes referred to as “quantum cryptography.” This approach taps into quantum phenomena to transmit an encryption key in such a way that its quantum state measurably changes when the message is read. This means that even a quantum computer-equipped hacker would not be able to intercept the encryption key without giving themselves away.
In theory, this provides an extremely secure way to transmit encryption keys, but it can be challenging to implement properly in practice and it can’t do everything that public-key cryptography approaches can (such as authenticating who you’re actually speaking with).
National security-minded agencies like the NSA have also warned that QKD introduces other forms of risk. For example, since QKD systems are designed to fail if someone intercepts the transmission, it actually provides a way for an adversary to cause problems by intentionally interrupting communications.
The technology also currently requires specialized equipment and is limited to relatively short distances (though new QKD distance records are regularly being set).
Despite these challenges, QKD is gaining traction and will become more common in the future. Toshiba, for example, is expecting to generate $3B in revenue from QKD services by the end of the decade. A growing number of quantum communication startups — including SpeQtral, Quantum Xchange, and KETS — are also working on QKD systems.
However, the tech will likely have to be deployed alongside other cybersecurity measures, including post-quantum cryptography, to be effective.
Given the above, companies should not think of QKD as an alternative to PQC but as a complementary cybersecurity tool that could be useful for specific applications related to some high-value data.
CB Insights clients can check out our quantum tech market map here and can see many more quantum key distribution companies in our Quantum Tech Expert Collection.
What’s ahead for post-quantum cryptography?
Post-quantum cryptography is already gaining momentum with businesses, but interest will surge when NIST announces its PQC standards.
More vendors are also entering the space. Early-stage startups like QuSecure, Code-X, and QANplatform have raised funding this year to build out quantum-resistant tech. Expect more players to spring up as demand for post-quantum cryptography products grows over the coming months and years.
Quantum computers are advancing rapidly and companies should continue to monitor the space. Funding is pouring into startups, quantum computing-related patents are on the rise, and new developments are regularly being announced. Tech giants like Google, Microsoft, and Amazon are betting big on the tech. Though the trajectory of the emerging quantum technology space is uncertain, the likelihood of a powerful quantum computer emerging in the not-too-distant future feels higher than ever.
Companies that balance the urgency of migrating to PQC alongside steady, deliberate decision-making stand to be most well-positioned. Moving too quickly presents pitfalls, especially around interoperability or being hamstrung by hard-to-fix constraints, but waiting until a powerful quantum computer is about to be launched would be far too late.
Cybersecurity risks aside, powerful quantum computers have disruptive applications across a wide range of industries, including finance, healthcare, logistics, and more — find out more in this report.
If you aren’t already a client, sign up for a free trial to learn more about our platform.